SolarWinds malware attack
Jump to navigation
Jump to search

Technical sources
- Highly Evasive Attacker Leverages SolarWinds Supply Chain to Compromise Multiple Global Victims With SUNBURST Backdoor - FireEye, December 13, 2020
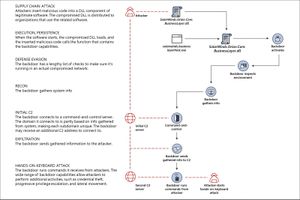
- FireEye has uncovered a widespread campaign, that we are tracking as UNC2452. The actors behind this campaign gained access to numerous public and private organizations around the world. They gained access to victims via trojanized updates to SolarWind’s Orion IT monitoring and management software. This campaign may have begun as early as Spring 2020 and is currently ongoing. Post compromise activity following this supply chain compromise has included lateral movement and data theft. The campaign is the work of a highly skilled actor and the operation was conducted with significant operational security.
- Mitigate SolarWinds Orion Code Compromise - Emergency Directive 21-01 - CISA, December 13, 2020
- However, operating such older versions carries significant risk, because (1) like other types of older software, older versions of SolarWinds Orion contain known vulnerabilities; (2) the adversary that inserted the SolarWinds Orion backdoor is likely to be intimately familiar with SolarWinds Orion code, including known or unknown vulnerabilities that may exist separate and apart from the backdoor; and (3) this adversary has demonstrated the capability and willingness to exploit SolarWinds Orion to compromise U.S. government agencies, critical infrastructure entities, and private organizations.
- SolarWinds advanced cyberattack: What happened and what to do now - Malwarebytes, December 14, 2020
- We learned more about the sophisticated attack first disclosed on December 8 when security firm FireEye reported it had been the victim of a state-sponsored adversary that stole Red Team assessment tools.
- On December 13 there was a new development when IT company SolarWinds announced it had been hacked and that its compromised software channel was used to push out malicious updates onto 18,000 of its Orion platform customers.
- This scenario, referred to as a supply-chain attack, is perhaps the most devious and difficult to detect as it relies on software that has already been trusted and that can be widely distributed at once. Among the victims who received the malicious update are FireEye, Microsoft and the US Treasury and Commerce departments, making this one of the biggest cyber incidents we have witnessed in years.
- New Evidence Suggests SolarWinds' Codebase Was Hacked to Inject Backdoor - Ravie Lakshmanan, Hacker News, December 16, 2020
- The idea, according to Pericin, was to compromise the build system, quietly inject their own code in the source code of the software, wait for the company to compile, sign packages and at last, verify if their modifications show up in the newly released updates as expected.
- SolarWinds Security Advisory - December 27, 2020
- SolarWinds was the victim of a cyberattack to our systems that inserted a vulnerability (SUNBURST) within our Orion® Platform software builds for versions 2019.4 HF 5, 2020.2 with no hotfix installed, and 2020.2 HF 1, which, if present and activated, could potentially allow an attacker to compromise the server on which the Orion products run. This attack was a very sophisticated supply chain attack, which refers to a disruption in a standard process resulting in a compromised result with a goal of being able to attack subsequent users of the software. In this case, it appears that the code was intended to be used in a targeted way as its exploitation requires manual intervention. We’ve been advised that the nature of this attack indicates that it may have been conducted by an outside nation state, but SolarWinds has not verified the identity of the attacker.
News sources

America say Putin did it
- U.S. Cyber Agency: SolarWinds Attack Hitting Local Governments - NPR, December 24, 2020
- SolarWinds says that nearly 18,000 of its customers received the software update that included the malware from March to June of this year.
- Russia's foreign intelligence service, the SVR, is believed to have carried out the hack. Kremlin officials have denied this charge.
- Lawmakers set to grill SolarWinds CEO on devastating hack - CNN, February 23, 2021
- Senior figures from three of the leading firms on the hunt, Microsoft and the cybersecurity firms CrowdStrike and FireEye, will also be testifying Tuesday alongside the SolarWinds CEO before the Senate Intelligence Committee.
Propaganda
- Lou Dobbs Tonight - Fox News via Facebook, December 25, 2020 (paywall)
Allegations
- US Defense Chief Nominee Claims Russia Should Be Held Accountable for Recent Cyber Attack - Sputnik, January 19, 2021
- US Reportedly Preparing to Sanction Russia Over Solarwinds Hacks, Navalny - Sputnik, February 23, 2021
- US Mulls New Measures Against Russia in Coordination With European Allies, Report Claims - Sputnik, April 15, 2021
- SolarWinds Hacking Claim a 'False Flag' by US Intelligence Seeking More Funding, Moscow Says - Sputnik, May 13, 2021
- Russia ‘Cozy Bear’ Breached GOP as Ransomware Attack Hit - Bloomberg, July 6, 2021
- Bloomberg Claims 'Cozy Bear' Hacker Group Breached RNC During Keseya Attack, RNC Denies Breach - Sputnik, July 6, 2021
Analysis
- The SolarWinds cyberattack: The hack, the victims, and what we know - Lawrence Abrams, December 19, 2020
- To Blame Russia For Cyber-Intrusions Is Delusional - A Treaty Is The Only Way To Prevent More Damage - Moon of Alabama, December 19, 2020
- The Deep State Will Not Dial Down Hacking - Bill Blunden, The American Conservative, January 4, 2021
- Another Mega Group Spy Scandal? Samanage, Sabotage, And The SolarWinds Hack - Whitney Webb, Unlimited Hangout, January 22, 2021
- Google shuts down a hacking operation being conducted by ally of the US government - Kevin Reed, WSWS, March 30, 2021
- Microsoft Blames Russia For Failure To Enforce Its Vendors Account Security - Moon of Alabama, October 25, 2021