Talk:SolarWinds malware attack
NSA and CIA did it?
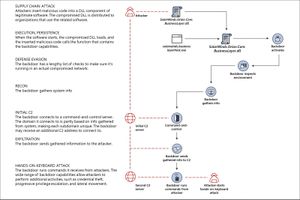
Someone found out the SolarWinds SNMP software contained malware that enabled remote access. The software was used in many government organizations in the US and elsewhere. So far no evidence has been presented that any of these organizations were actually attacked.
Cyber attribution is usually impossible. It is equally likely that the malware was inserted by US actors. I doubt that this "sophisticated supply chain attack" would have been possible without US insiders in the company.
Update: Actually we know that this was an inside job by US actors and intelligence services. No Russian mole could insert the spyware functionality into the source code. More likely the whole software team was compromised. The attack vector must have been part of the specification of the software. Proof of this comes from the fact that it has taken over two weeks and SolarWinds still has not fixed the problem. The spyware must be so embedded with the rest of tho software that they would not know what to remove. They have the source code, yet they have not published any part of it. Quote:
- Additionally, we want you to know that, while our investigations are early and ongoing, based on our investigations to date, we are not aware that this SUNBURST vulnerability affects other versions of Orion Platform products.
-- Petri Krohn (talk) 11:12, 29 December 2020 (UTC)